pen testing thick client applications|thick client pentest : China The configuration files are usually readable by all operating system users, which allows anyone who can read the file access to the compromised resources. The following table presents a set of tools aimed for locating sensitive data storage on files and registry: Usually, a thick client application contains several configuration files in the root f. See more WEB16 de set. de 2022 · Siga o PORTAL DO ZACARIAS no Facebook, Twitter e no Instagram. Entre no nosso Grupo de WhatApp e Telegram . Sem mais informações. VEJA VÍDEO: LEIA MAIS. Homem abandonado em calçada por amigos morre após ser atropelado. VEJA VÍDEO. Guardas arrastam homem pelo pé e o seguram pelo pescoço durante .
{plog:ftitle_list}
webJoined May 2020. 29 Following. 259 Followers. 猫です @ahoo08__. about 16 hours ago. @Tanosimi3500 @wareyeknee インプ稼ぎが言うの自虐的だな. 0 0. 猫です .
It is essential to understand the full functionality of the tested thick client application tested during a pentest. Moreover, it is important to navigate through all of the UI elements with multiple users. Each user might have different permissions and unique functionalities that need to be discovered. For example, the . See moreSo, now that we’ve identified the development language used to build the tested thick client application we tested. The next step is to sniff the traffic between that thick client application and the . See more
Applications usually store information in local files and the registry. Sensitive information that we might look for in a thick client pentest includes: 1. Usernames 2. Passwords 3. Connection Strings . See moreThe next step is to examine if the tested thick client application is vulnerable to a DLL hijacking vulnerability. DLL hijacking is an attack that exploits the Windows search and load algorithm, allowing an attacker to inject code into an application through disk manipulation. In other words, simply putting a DLL file in the right place causes a vu. See moreThe configuration files are usually readable by all operating system users, which allows anyone who can read the file access to the compromised resources. The following table presents a set of tools aimed for locating sensitive data storage on files and registry: Usually, a thick client application contains several configuration files in the root f. See more
Thick client application penetration testing entails studying the application’s business logic to find and correct any weaknesses that might be used to jeopardize the system’s operation. 10. Data Tampering. Thick client .When it comes to thick client penetration testing, there are several tools that are commonly used by security professionals. One such tool is Burp Suite, which is a powerful platform for performing security testing of web applications.It .
As we have understood what thick client is and its architecture, now we’ll move on to the penetration testing approach. We have shown some vulnerabilities of thick client. Starting checks (Enumeration) Application .
Thick client (Desktop) application penetration testing is the process of evaluating the security of a thick client application by simulating attacks to identify vulnerabilities. A thick client application, also known as a fat client , is a software program that runs on a local machine and communicates with a server or a database to perform its .This course introduces students to the penetration testing concepts associated with Thick Client Applications. This is an entry level to intermediate level course and we encourage you to take this course if you are interested to learn Thick Client Application Security.
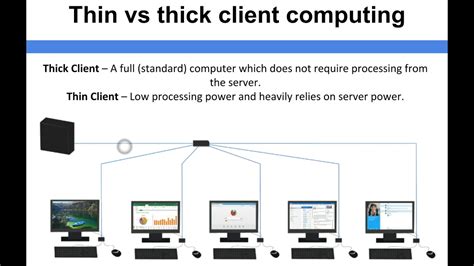
thin client vs thick client
moisture meter 20 readings
Information gathering is a critical initial phase in thick client application penetration testing, focused on collecting detailed data about the application’s architecture, components, and interactions with servers. This phase aims to identify communication protocols and potential entry points for exploitation. Conclusion. This blog highlights different tools and approaches for testing a thick client application for vulnerabilities. The tools have remained the same over a period of time and there are no major changes in the way thick client applications have been assessed when compared to web / mobile applications, where introduction of new frameworks / technologies .
A practical guide to pentesting thick client applications. . Thick Client Application Penetration Testing Course Introduction Course Introduction (1:37) Help and Support Downloadables Introduction and Lab Setup Introduction to Thick Client Applications (4:12) Lab Setup - Part 1 (2:04) Lab Setup - Part 2 (18:44) . In this series of articles, we will learn various tools and techniques used to perform thick client application penetration testing. A step by step breakdown being deployed, we will discuss about starting with the very basics to the advanced test cases. Introduction . Referenced under multiple names, such as: Fat client/Heavy client/Rich client .Discover hidden vulnerabilities in windows thick client applications! Master thick client pentesting with our comprehensive course. Learn thick client pentesting tools, methodologies and exploits - enroll now! . Enrol on a thick client penetration testing course to get an insight into the thick client penetration testing methodology. Learn .
In this blog post we will delve into the process of testing Linux thick client application to identify and address potential security vulnerabilities, by exploring various testing techniques and tools. . Memory analysis is crucial in penetration testing thick client applications. It involves examining the contents of computer memory when the .Thick Client Penetration Testing aims to assess and ensure the secure deployment of thick client or native applications by simulating real-world attacks and analysing potential weaknesses. This comprehensive testing process helps uncover critical vulnerabilities that could be exploited by malicious actors, ensuring that the application’s .
moisture meter 919 charts
Thick client penetration testing is a security assessment process that focuses on identifying and mitigating vulnerabilities in applications that run on client devices, such as desktops or mobile.Enhance your cyber security with RBT Security's application penetration testing assessments, covering web, mobile, APIs, Thick Client penetration testing.Testing thick client applications for security vulnerabilities requires expert manual penetration testing skills and a thoughtful, methodical approach. NetSPI’s thick client app penetration testing uses multi-vector cybersecurity testing to identify design and configuration weaknesses. Proxy unaware thick client: Do not natively include proxy settings so the user is required to make some changes in the system’s host file Thick Client Testing Methodology. Currently, there is no definite methodology when .
GUI TESTING. Test For GUI Object Permission. Display hidden form object; Try to activate disabled functionalities; Try to uncover the masked password; Test GUI Content. Look for sensitive information; Test For GUI Logic. Try for .Thick Client Penetration Testing (a.k.a. Thick Client Pentest, Thick Client VAPT, Thick Client Pen Testing) identifies exploitable vulnerabilities on both the local and server-side. The attack surface is larger and requires a different approach from web application penetration testing. Such process often requires specialized tools and custom .
SecureLayer7 begins its thick client application pen testing service by understanding each application's intricacies and functionality. The methodology involves reverse engineering to identify hard-coded secrets, authentication weaknesses, insecure data handling, and potential client-side exploits like buffer overflows and injection attacks . Understanding Thick Client Penetration Testing. Thick client penetration testing is a proactive approach to evaluating and enhancing the security of applications that run locally on a user’s device. You can take the help of an experienced thick client application security testing, to deal with these issues. Risks in Thick Client Applications. Thick client applications can be exposed to a variety of security issues. Understanding these problems is important for implementing effective security measures. Improper Input Validation
In the rapidly evolving landscape of cybersecurity, organizations face an increasing challenge to secure their software applications and protect sensitive data. Among the arsenal of defense mechanisms, penetration testing, or "pen testing," has emerged as a vital practice to identify and mitigate vulnerabilities. In this article, we delve into the fascinating world of thick . Testing thick client applications, for example, requires patience and a systematic approach, and simple automated assessment scanning does not suffice. . and eWPTXv2. He has experience penetration testing with mobile apps, web applications, networks, cloud configurations, and thick-client apps. Bash, Python, Go, and PowerShell are his . If a thick client application has a built-in feature to set up a proxy server, then it is known as a proxy-aware Thick client. Testing these types of thick clients is easy and straightforward due .Learn practical thick client application penetration testing techniques. How to reverse engineer .NET binaries. Students will learn how to patch .NET binaries. How to identify and exploit common security issues in 2-tier applications. Learn multiple ways to intercept TCP traffic coming from thick client apps.
Importance of Pen Testing Thick Client Applications. Because thick client apps provide special security issues, pen testing is essential. Moreover, thick clients manage complicated functions and sensitive data while running on users’ devices. Hence, they are often the focus of cyberattacks. Penetration testing is necessary to find .
Selecting the method for Thick Client Pentesting. For thick client penetration testing, there are two key methods: Black-Box Testing: It is the testing approach where the testers initiate the test without any prior knowledge about the app’s configurations.They carry out the testing of all functionalities of the application without any access to design, operation, .
thin client vs pentest
moisture meter acceptable levels in plaster
webSabrina finalmente desistiu, ciente de que ela não significava nada para ele. Deitada na cama do hospital, ela assinou os papéis do divórcio com o coração partido. No entanto, esse não foi o fim para o casal. Após o divórcio, o homem que antes fora tão frio implorou: "Sabrina, cometi um grande erro. Por favor, não se divorcie de mim.
pen testing thick client applications|thick client pentest